Earlier in the smartphone days, they didn’t all come with a built-in ‘flashlight’ feature. It was one of the easiest apps in the world to make – all it does is toggle your camera flash off and on – so it was quickly created by app developers and added to Google’s app store.
Unfortunately, some bad actors saw opportunity in this. There were dozens of flashlight apps made and put on the Play store that did a lot more than turn on the camera light. Some played ads when you tried to do nearly anything on your phone. The more dangerous ones haven’t done anything – yet. But when people installed these apps, they used a pop-up prompt to ask the phone owner for dozens of permissions, including access to your contact list, access to record your calls, and even permission to create new contacts on your phone. Most people don’t read the fine print of these prompts; they just accept them. These apps have been downloaded tens of millions of times, and they’re all one update away from turning millions of phones into dangerous spying devices.
It’s Not Just Phones
Fast forward a few years, and this scheme has jumped beyond the smartphone app stores. One of the largest cybersecurity firms fell prey to one of these pop-up prompt attacks, and lost 28,000 items of personally identifiable data – the exact type of data they train their customers to protect.
An employee at SANS received an email that looked like it came from the company’s internal SharePoint network. It showed a shared excel file that referenced a “July Bonus” being paid by the company. When the user clicked on it, they were directed to a page with a real Microsoft prompt, which indicated that an app was asking for permission to install itself to their Office365 account.
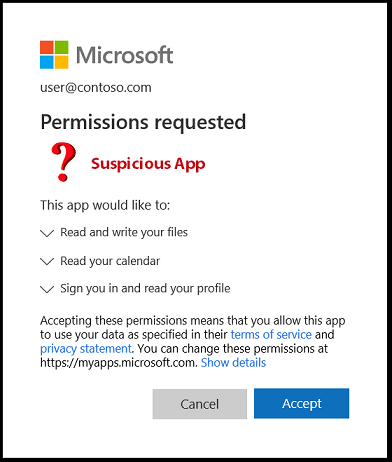 Unfortunately, the user granted that permission. The app created a forwarding rule that sent copies of emails with bank-related terms like “wire”, “payment” and “purchase” to an external email address. Many emails were forwarded before they discovered the ruse.
Unfortunately, the user granted that permission. The app created a forwarding rule that sent copies of emails with bank-related terms like “wire”, “payment” and “purchase” to an external email address. Many emails were forwarded before they discovered the ruse.
Don’t Fall Victim to These Schemes
Both of these stories are lessons to make sure you know exactly who or what is getting permission to access your information, and what information they can access, before you grant it. The reason these prompts are presented is because an application is requesting to access something that might be sensitive. If you weren’t expecting to get the prompt, or if the prompt is asking for permission to do things that aren’t relevant to the task at hand, don’t just say ‘yes’ to make the prompt go away.
Also, always remember that it’s safer to follow directions being given out by a third party if you contacted them for help. Many companies have policies against giving out sensitive company information without verifying the identity of the person on the other end of the call. One way to do this is to always make sure that you initiate the call, and that the phone number you dial to reach the person has been verified by a trusted source (such as a company website).
The same is true for any access you grant for third-party applications to access your data. Never grant these types of permissions if they’re prompted by clicking a link in an email you didn’t ask to receive. If you need to install a trusted third-party add-on, go to the developer’s website and follow the official link to do so.
To learn how WingSwept can help protect your company’s sensitive data, call us at (919) 600-5190 or email us at Team_WingSwept@WingSwept.com.
